Hello everyone,
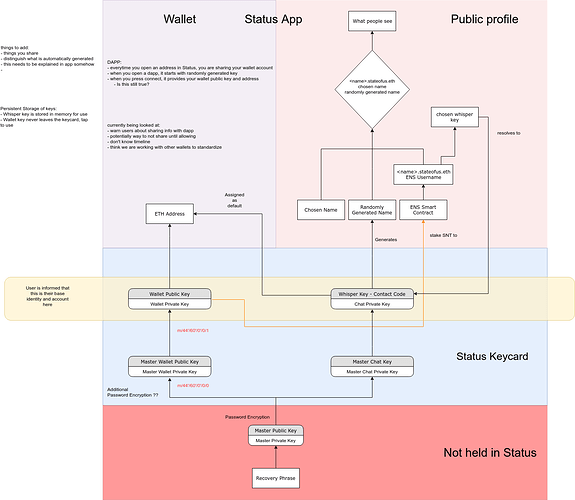
we had a lot of discussions about decoupling the whisper and wallet key after this topic and now we need to implement it to be able to finish the hardware wallet implementation, so that wallet keys remain on the card, and whisper keys can be downloaded to the phone during a session to be able to encrypt/decrypt messages.
The big change will be that the wallet address won’t be derivable from the whisper identity (public key), so without supporting multiple wallets it won’t be possible to send/receive a transaction in a chat without asking for the wallet address with some kind of interaction.
The options that we have are:
1 - updating the chat protocol so that user A can send a wallet address request to user B. User B can accept and reveal its address. User A receives the address and can now send the transaction.
2 - update status-go to and status-react to support multiple wallets and whisper identities. At this point it would be possible to send a chat transaction without interaction, and user B will receive the transaction in the chat address without revealing the main wallet. User B will be able to manage standard BIP44 wallets + the ones derived from the whisper identities.
3 - combine option 1 and 2 so that the whisper and wallet keys are decoupled and chat transactions are sent to the right wallet address.
Since we want to support multiple identities anyway, I think options 2 and 3 are the best ones; option 1 would only be temporary.
If we agree on supporting multiple wallet/whisper keys (sub-accounts) for each account the steps I would like to work on are:
1 - update our go-ethereum patches to save the BIP44 parent key in the main accout keystore file. This will allow to create sub-accounts that are BIP44 compatible. In the current implementation we save the second BIP44 key as a parent extended key to derive sub-accounts, but those addresses will end up having a non-standard derivation path m/44'/60'/0'/0/1/n (where n is the index of the sub-account).
2 - update status-go account creation to create 2 initial key pairs for each account. One for the wallet and one for whisper using a different path that we are trying to propose in the EIPs repository. Each key pair will have an extended key to derive sub wallet/whisper identities.
At this point status-react should be able to create multiple identities using the parent extended key saved in the main account key-pairs, and show multiple wallets.
If we want to implement only the options 2, we only need some support from the wallet team. In case we want to support 1 or 3, we need more support and changes from the chat team as well.
What do you think about it?